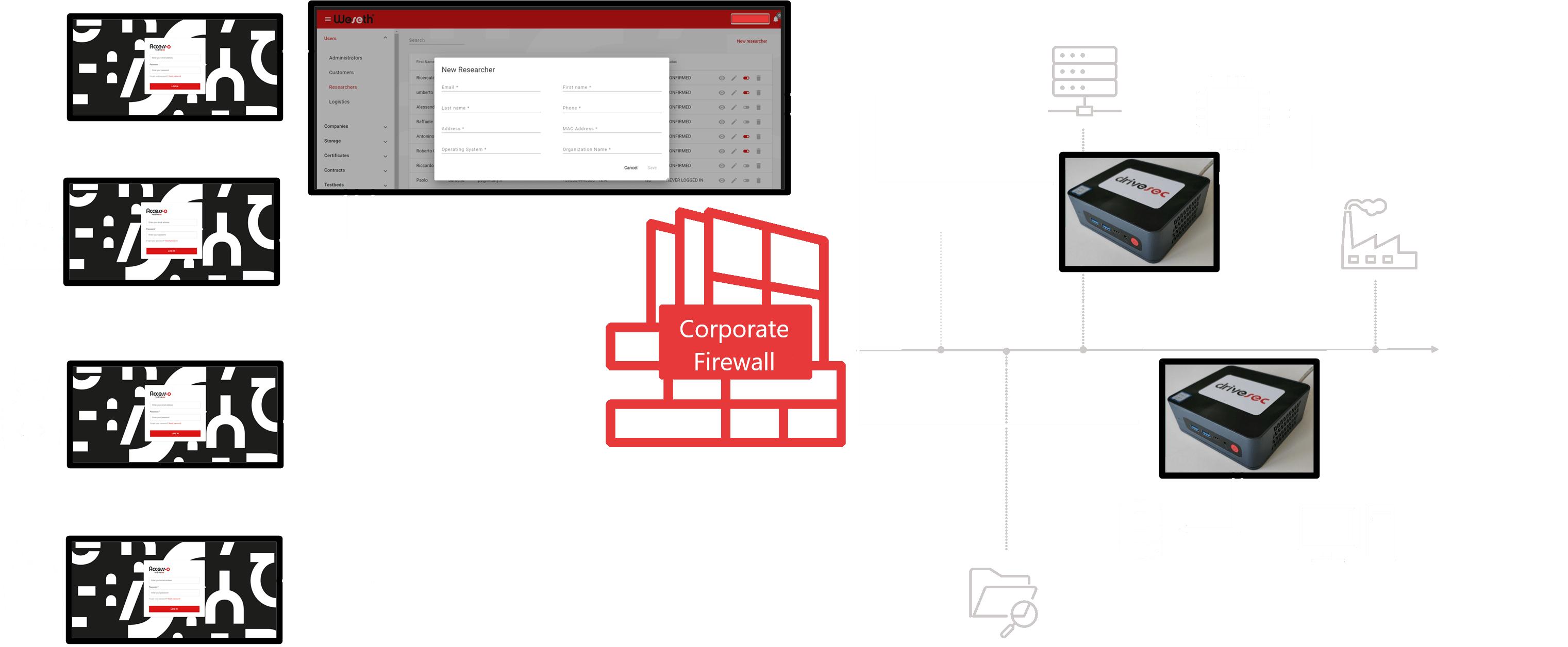
Access-o allows secure remote access to any Company TCP/IP-based
resources using an on-demand Point-to-Point link.
Access-o utilizes a security framework that enforces mandatory strong
authentication for all users and roles.
Remote, on-demand access guarantees convenient connectivity via secure
channels using state-of-the-art cryptography for confidentiality, integrity,
and data authentication.
resources using an on-demand Point-to-Point link.
Access-o utilizes a security framework that enforces mandatory strong
authentication for all users and roles.
Remote, on-demand access guarantees convenient connectivity via secure
channels using state-of-the-art cryptography for confidentiality, integrity,
and data authentication.
Advantages of using Access-o
-
Access-o is designed for remote and external users to easily share access to critical Company resources, such as manufacturing systems, servers, legacy systems, data repository, 3D printers, etc.
-
Compared to traditional VPN solutions, Access-orequires nearly zero setup time and no SW installation or configuration on the target resource. It’s so autonomous that it doesn’t rely on any Company IT infrastructure.
-
Access-o enables the forwarding of weaker protocols, allowing users to manage insecure applications as usual while taking advantage of its security features.
Access-o uses the Drivesec-patented Weseth® platform
Weseth® does not rely on a Customer’s IT infrastructure – independently communicates with its own mobile technology.
Access-o can be seen as a secure pipe for all remotization activities. Access-o is designed to provide secure remote access to all engineers working from different locations. This makes engineering work more flexible, supports smart working, and optimises outsourcing strategies for engineering activities. Remote access can also simplify product design by reducing the number of benches needed.